December 2014 Patch Tuesday
Last updated on: October 27, 2022
It is December, time for our last Patch Tuesday of the year. Microsoft is publishing seven bulletins this month bringing the total count for the year to 85. Compared to 2013 with 106 and 2011 with 100 bulletins, 85 bulletins is not particularly high.
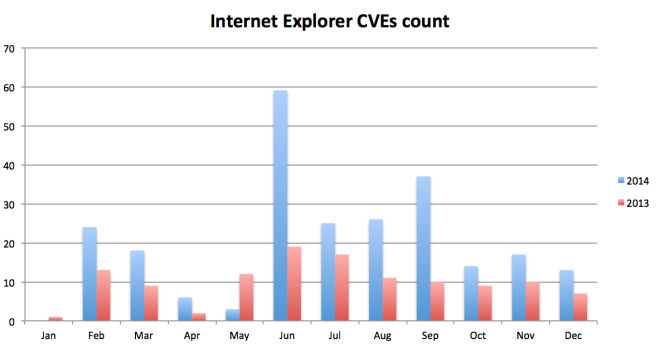
Nevertheless, 2014 has been quite dynamic with lots of issues that have surfaced in new and unexpected areas such as OpenSSL and Linux. We also had a larger number of 0-day vulnerabilities (vulnerabilities where the information is in the wild before the patch) this year. Counting both Microsoft and Adobe we had 24 bulletins that acknowledged that vulnerabilities were publicly known before a patch could be delivered. Further we saw Internet Explorer under intense scrutiny by security researchers leading to a large number of addressed CVEs, an effect which has only recently slowed down with Microsoft’s changes to the memory allocation process in IE.
But back to this month’s patches. There are five patches that can lead to Remote Code Execution (RCE) which are the most critical flaws:
- MS14-080 for Internet Explorer and MS14-084 for VBscript. Both have a malicious webpage as the main attack vector, i.e. a website controlled by the attacker, think for example the 100s of thousands Drupal sites that recently became exploitable through a SQL injection vulnerability in a core component.
- MS14-081 in Word, MS14-083 in Excel and MS14-082 in an Office component. Here the attack vector is a malicious document that the targeted user has to open and that will then exploit the vulnerability to gain control over the user’s machine. Attackers have become very proficient in these types of attacks by adapting the document title and content in question to the interests of the target and document attacks are quite successful.
The remaining two bulletins address problems in Microsoft Exchange’s Outlook Web Access (OWA) component and a graphics library in Windows. The Exchange patch was supposed to be released last week, but was held back due to some last minute testing issues. The graphics library flaw on the other hand can be used to gain information about the machine’s memory layout, so it is a vulnerability that has an auxiliary function. In an attack it provides useful information, but needs to be paired with another vulnerability to gain control over the user’s machine.
Adobe is also releasing two security advisories, both labeled as critical meaning they can be used to gain RCE. APSB14-27 is an update for Adobe Flash and APSB14-28 is a new version of Adobe Reader and Acrobat. We recommend applying these patches as quickly as possible as attackers often use the Flash and PDF vector in their campaigns. Users of Google Chrome and Internet Explorer 10 or 11 get the Flash update delivered automatically – others need to download the latest versions from Adobe directly.
Lastly there was an update to October’s POODLE vulnerability. The original documented flaw was limited to SSL v3. It can be used to decode encrypted user data, if the attacker has some control over the victim’s browser. This POODLE vulnerability itself cannot be fixed as it is a flaw in the SSL protocol specification. The only way to address it is to stop using SSL v3 on both the server and client side. Mozilla Firefox has already eliminated SSL v3 from its current version (v34) and Google Chrome will do the same in its coming version 40.
But POODLE is spreading; yesterday Adam Langley from Google announced that POODLE also affects certain implementations of TLS, which before was deemed immune to the problem. However in the TLS case it is a patchable, most likely caused by source code reuse for the padding decoding from an SSL implementation. SSL accelerators from F5 and A10 networks are affected – look for patches from your vendors if you run any of these equipments. Qualys’ SSLLabs has a detection for this new flaw (CVE-2014-8730) built-in as of yesterday and you can use it to check on your public websites. Take a look at Ivan Ristic’s blog post "POODLE bites TLS" for more details.
Stay tuned for more updates on this blog.